Mastering Cyber Kill Chain: Defending Against Cyber Threats
The cyber kill chain is a concept used in cybersecurity to describe the stages of a cyberattack, from the initial reconnaissance to the final objective. Understanding the cyber kill chain is essential for both cybersecurity specialists as it provides a structured way to analyse and defend against potential threats. Let’s break these stages down.
What is the Cyber Kill Chain?
The cyber kill chain is a framework that outlines the various stages an attacker goes through in planning and executing a cyberattack. It was originally developed by Lockheed Martin and has since become a widely accepted model for analysing and defending against cyber threats.
The Stages of the Cyber Kill Chain
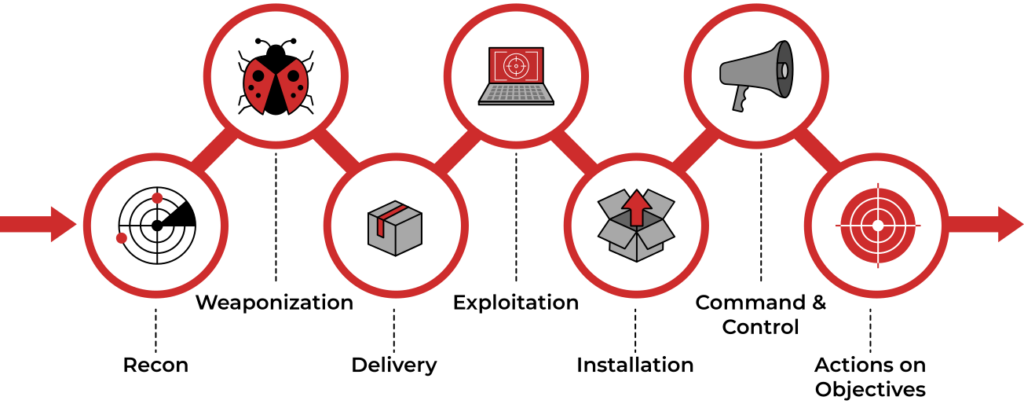
- Reconnaissance: In this initial phase, the attacker gathers information about the target, such as identifying vulnerabilities, potential entry points, and weaknesses in the target’s security posture. This can involve passive information gathering, like scanning publicly available data or conducting open-source intelligence (OSINT) research.
- Weaponization: During this stage, the attacker creates or acquires the malicious tools or exploits needed for the attack. This can include crafting malware, developing phishing emails, or preparing malicious payloads.
- Delivery: The attacker delivers the weaponized content to the target, often through various means like email attachments, infected websites, or other vectors. The goal is to get the malicious content onto the target’s system.
- Exploitation: At this point, the attacker exploits vulnerabilities in the target’s system to gain access. This could involve using software vulnerabilities, exploiting misconfigurations, or social engineering to trick users into opening malicious files.
- Installation: The attacker establishes a foothold within the target’s environment by installing backdoors, remote access tools, or other malware. This ensures persistent access for future stages of the attack.
- Command and Control (C2): Once inside the target’s network, the attacker establishes communication channels with the compromised system(s). This allows them to control and manage their illicit activities while avoiding detection.
- Actions on Objectives: The final stage involves the attacker achieving their primary goal, which could be data theft, system compromise, or other malicious objectives. This is often where the most damage is done.
Why is the Cyber Kill Chain Important?
Understanding the cyber kill chain is crucial for cybersecurity specialists because it provides a structured way to analyse and defend against threats. By identifying and disrupting the attack chain at an early stage, security professionals can prevent cyberattacks from reaching their ultimate objectives. It’s a proactive approach to cybersecurity that helps in designing effective security strategies and incident response plans.
Question 1: What is the primary purpose of the Cyber Kill Chain framework?
a) To facilitate cyberattacks
b) To analyze and defend against cyber threats
c) To automate network security
d) To create malware payloads
Question 2: At which stage of the Cyber Kill Chain does an attacker gather information about the target, such as vulnerabilities and weaknesses?
a) Weaponization
b) Exploitation
c) Reconnaissance
d) Command and Control (C2)
Question 3: In the context of the Cyber Kill Chain, what is the “Delivery” stage primarily focused on?
a) Controlling compromised systems
b) Establishing communication channels
c) Gaining access through exploitation
d) Getting malicious content to the target
Question 4: What is the final objective of an attacker in the Cyber Kill Chain framework?
a) Establish communication channels
b) Install malware on the target system
c) Achieve the primary malicious goal
d) Gather information about the target
Question 5: How does understanding the Cyber Kill Chain benefit cybersecurity professionals?
a) It allows them to automate cyberattacks
b) It provides a structured way to analyze and defend against threats
c) It helps create stronger malware payloads
d) It facilitates open communication with attackers
1b – 2c – 3d – 4c – 5b
